Two-factor authentication (2FA) has been a staple of digital security for decades. What began in the 1980s as a pioneering effort to secure access has evolved in response to increasingly complex threats and a growing demand for seamless user experiences.
The concept of using two independent factors to verify identity dates back to the introduction of the RSA SecurID token, which offered time-synchronized codes tied to a physical device. By 1986, smart cards had emerged, combining something the user has (the card) with something they know (a PIN), marking one of the earliest real-world applications of 2FA.
Since then, two-factor authentication has become a foundational element of digital security strategies, with industry leaders like Okta, Duo Security and Yubico driving widespread adoption.
While 2FA remains a key layer of defence, it comes with inherent limitations. This blog explores how eSIM technology, combined with cloud-native telecom solutions like Telecom-as-a-Service (TaaS), is enabling a new era of identity authentication that offers up a reimagined security layer that’s more streamlined, scalable and secure.
Why the shift toward two-factor authentication (2FA)
As digital ecosystems expanded, so did the attack surface. Cybercriminals grew more sophisticated, social engineering techniques became widespread, and legacy authentication methods began to show their age.

Key drivers behind the evolution of 2FA:
- Increased threat sophistication: The 2022 Data Breach Investigations Report found that 82% of breaches stemmed from social engineering or human error.
- User experience demands: As consumers expect instant, frictionless access, security measures must balance usability with protection.
- Technology advancements: The proliferation of smartphones, tablets and IoT devices has created new vectors for attack—and new opportunities for security innovation.
Why eSIM could be the next security frontier
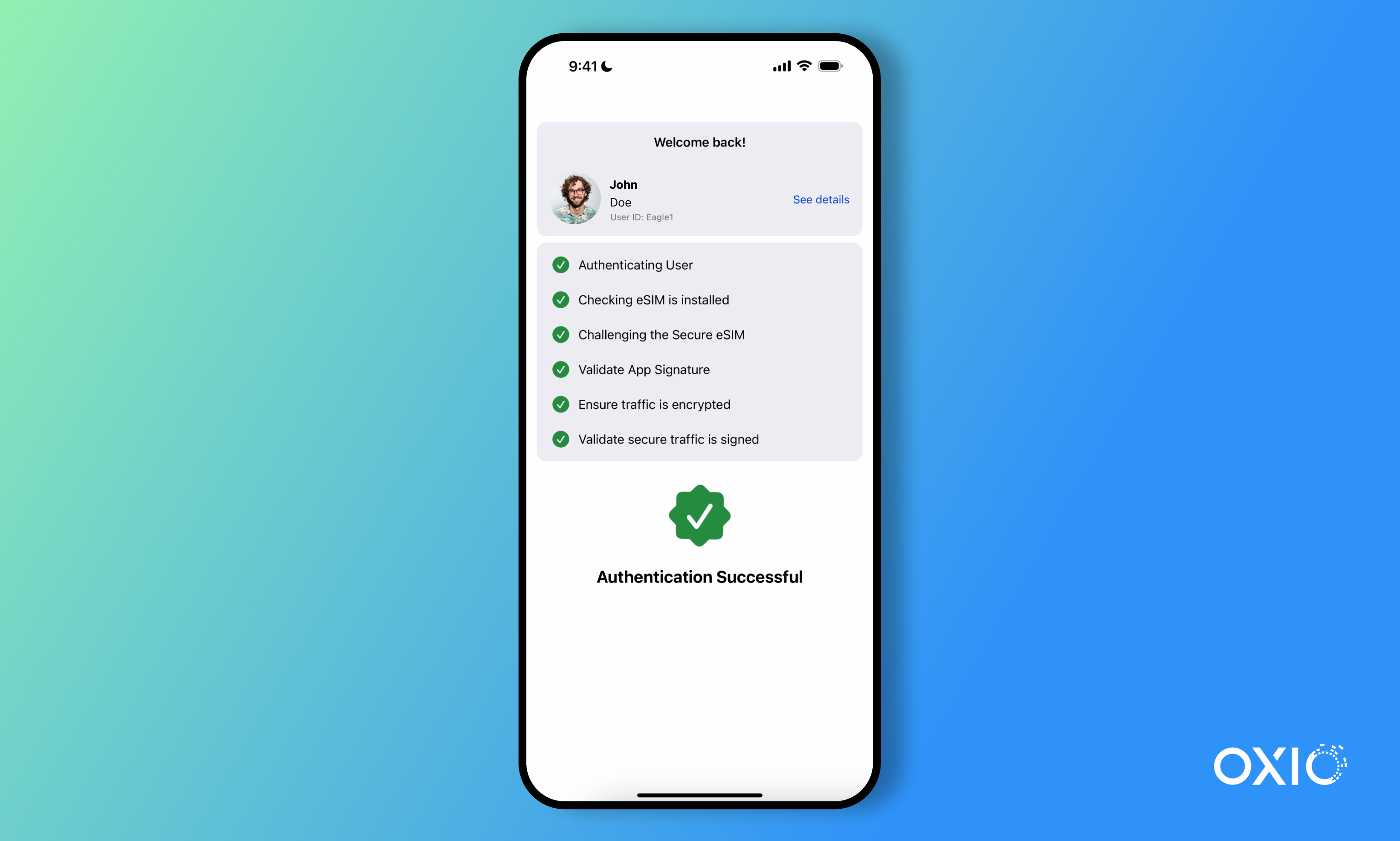
Although 2FA has gained significant market traction over the past few decades, it has its own limitations and security risks. As cyber threats become more sophisticated, we’ll start to see new and more robust identity layers being introduced to combat this growing threat. One viable option is the introduction of eSIM as a secure and tamper-resistant identity layer that’s embedded directly into device hardware.
Unlike SMS-based 2FA, which is vulnerable to phishing and SIM-swap attacks, eSIM authentication is device-bound and encrypted, significantly reducing the attack surface. It eliminates dependency on third-party apps or networks, streamlines the user experience and supports scalable deployment across enterprise fleets and IoT ecosystems. As digital identity becomes increasingly critical to zero-trust architecture, eSIM positions itself as a seamless, secure, and always-on identity credential, aligning with next-generation security frameworks and mobility strategies.
eSIM authentication offers a step-change in how identity is handled:
- Embedded security: Identity is tied to the hardware and telecom layer, not an app or a password.
- Resilient architecture: No reliance on SMS, email or user-entered codes—just seamless, silent validation.
- Scalable deployment: With companies that can offer global APIs, businesses can launch secure, cross-border authentication flows in weeks, not months.
The pitfalls of traditional two-factor authentication (2FA)
While 2FA has generally improved security over single-factor methods, it is far from immune to attack. Many breaches today still occur despite 2FA due to the following vulnerabilities:
- Phishing: Users may unknowingly provide both their credentials and 2FA codes to attackers via deceptive emails.
- Session hijacking and cookie theft: As noted in this video by renowned hacker Kevin Mitnick, if an attacker gains access to a cookie, often via XSS or phishing, they can then impersonate the victim without needing credentials or 2FA, and the victim is often none the wiser.
- Man-in-the-Middle (MitM) attacks: These intercept communications between the user and the service, capturing 2FA codes in real-time. Corporate employees using public Wi-Fi without a VPN can often be in danger of a MitM attack.
- SIM swapping: Fraudsters exploit telecom vulnerabilities to redirect SMS-based 2FA messages, effectively taking over user accounts. We can look back to 2019 when Twitter CEO Jack Dorsey’s account was hacked via a SIM swap. This led to 15 minutes of highly offensive and racist remarks being sent out via his account.
- Push notification fatigue (MFA fatigue): Attackers flood users with repeated 2FA push requests. Eventually, out of confusion or frustration, a user approves one. This exploit targets user behavior rather than technical flaws. A recent example of this is the 2022 Uber breach where an attacker gained access to a contractor’s account credentials and used them to log in, triggering multiple MFA push notifications. Eventually, one of these was accepted, granting the attacker unauthorized access to Uber’s internal systems.
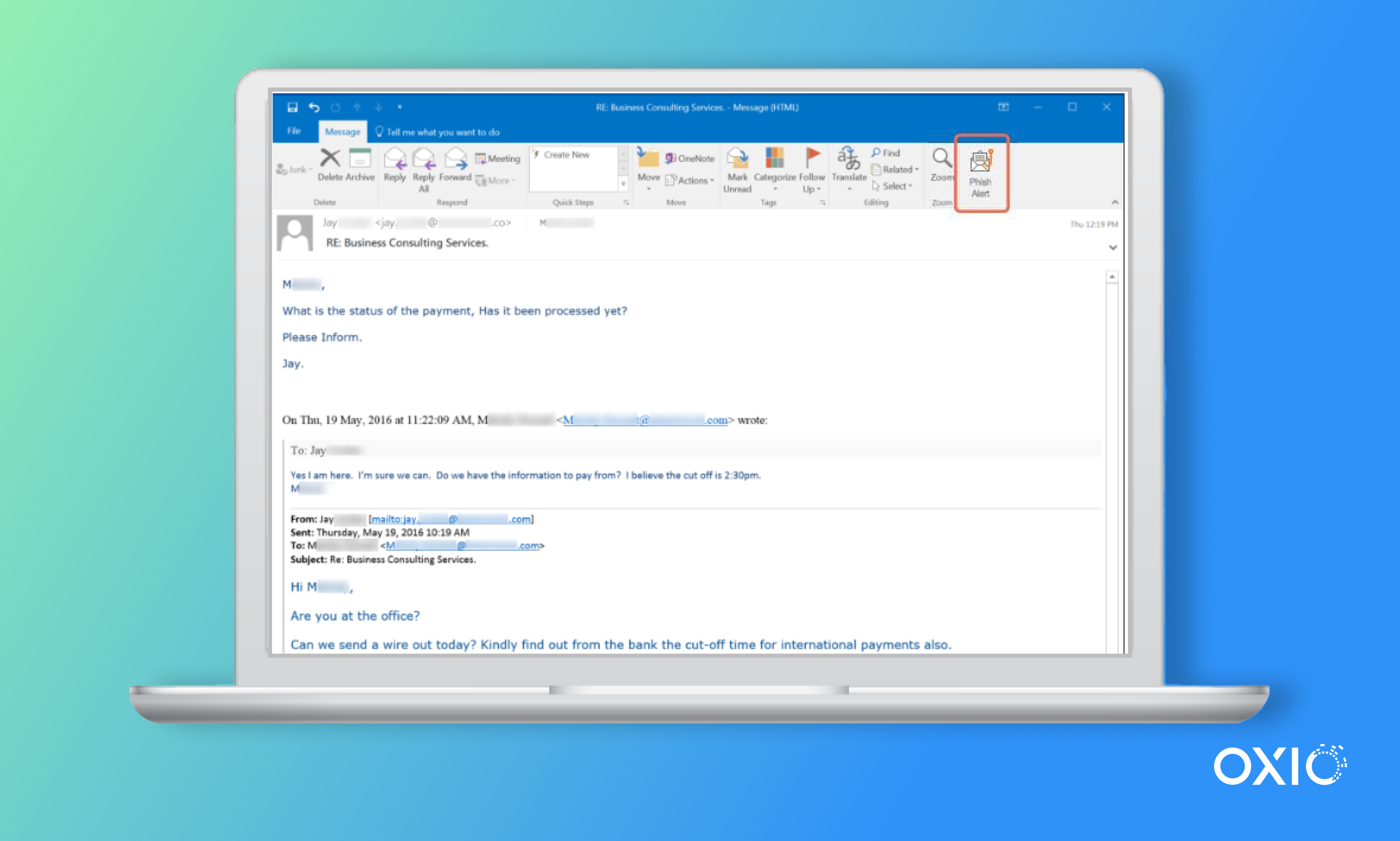
Regardless of company size or internal safeguards, the examples above show how even the most well-defended organizations can fall victim to identity fraud and cyber-attacks, highlighting the urgent need to rethink the future of online identity security.
What comes next for authentication: A new foundation for trust
The future of authentication lies beyond patchwork fixes and incremental upgrades. The shift is toward decentralized identities, AI-driven threat detection and hardware-bound authentication that eliminates human error from the equation.
At the forefront of this evolution is OXIO, a pioneer in Telecom-as-a-Service (TaaS). By turning the eSIM into a programmable, persistent identity layer, OXIO is reimagining how authentication is done—from the network up.
From 2FA to built-in trust with TaaS
What used to take 12 to 18 months and millions in integration costs with mobile operators can now be executed in weeks through OXIO’s TaaS platform. This creates a streamlined pathway for any enterprise to embed authentication directly into their apps—no friction, no middlemen, no weak links.
The result? A radically improved user experience and a fundamentally more secure digital identity framework.
Authentication isn’t just evolving, it’s being redefined. With eSIM and TaaS, we’re not just improving 2FA. We’re building trust into the fabric of the network.
For more information on OXIO’s Telecom-as-a-Service (TaaS) solution, get in contact today.
